Note: The examples in this write-up are employed for the function of creating the technical ideas far more understandable to readers, so they have been simplified from the real facts. Readers are encouraged to accept these examples openly and in excellent faith.
Five in the morning.
The sound of a police car or truck could be heard in front of the residence.
“You have been arrested.”
Jack wakes up and isn’t going to know why. Everything was like a actual nightmare.
Jack is dragged away and questioned about several issues as a extremely harmful smuggler.
Jack was baffled. He was wholly pure, how the hell did his title, date of birth and financial institution account amount coincide, as if another person had lived yet another sinful lifestyle in his picture of him?
A stolen lifestyle.
Jack’s privacy has been severely violated and he now faces imprisonment for the rest of his lifestyle. However, remarkably, a handful of days ahead of the sentencing, the jury acquired an anonymous letter stating that Jack was not the culprit and that the sender of the letter knew the precise area of the criminal, in which the actual culprit is, but not you are permitted to reveal your identity right in this letter. If the jury and the sender of the letter had a personal meeting to talk about, it would be challenging for the public to think that the two sides did not agree to frame yet another innocent individual.

So how can the sender reveal the genuine culprit’s identity transparently but not publicly to clear Jack?
Transparency can be assured by the exchange through blockchain and privacy can be pleased by a far more unique mechanism. In today’s write-up, the Kyros Research crew will introduce readers to the mechanisms now employed by unique blockchain platforms to make sure the privacy of the folks participating in their network.
one. Reliable execution surroundings
Put just, in the Trusted Execution Environment (TEE), the information will be stored separate from the other elements of the processor, therefore defending them from attacks by external agents. On the blockchain, this implies that validators are unable to know the compute information within. Secret Network and Oasis Network are two blockchain platforms that use this engineering, namely the SGX processor (Software Protection Extensions) from Intel, committed to delivering a TEE for delicate information.
Therefore, if the anonymous mailer contacted the jury to reveal details about the actual culprit by this kind of blockchain platforms, they would not have to fret significantly about the authenticity of the letter’s letter to the jury, and the public can rest assured that neither get together – the sender of the letter. and the jury – they are not colluding to pin the blame on everyone else.
However, this alternative even now has disadvantages. The SGX processor has a employing that only the central processing unit (CPU) is trustworthy, so storing confidential details right here and isolating it would be a risk-free alternative. This is the assumption that has led to the danger that the lousy guys do not right assault the protection procedure of the personal computer but make a “detour”, or the so-identified as “detour”. side channel attachment.
Another difficulty when applying TEEs in the blockchain is the downgrade assault (return assault). The most important trigger of this difficulty is that the state of a blockchain is normally feasible reverse rewind, and the exact same “privacy” supplied by TEEs will abet this wrongdoing.
two. Mixing
Mixnet is a mechanism employed by the NYM Network. In the mixnet, the transaction path will be “cleared”, creating it unattainable for outsiders to locate unique details in these transactions.
Specifically, NYM’s mixnet network is like an up to date edition of Onion Routing, a system of making sure anonymity when communicating inside of a personal computer procedure. In this system, a message will be split into several smaller packets and these smaller packets will be encrypted in flip by several layers in the delivery procedure to the location. Mixnet will take this technique a stage additional by scrambling the encrypted packets, creating it even far more tricky to locate the unique message.
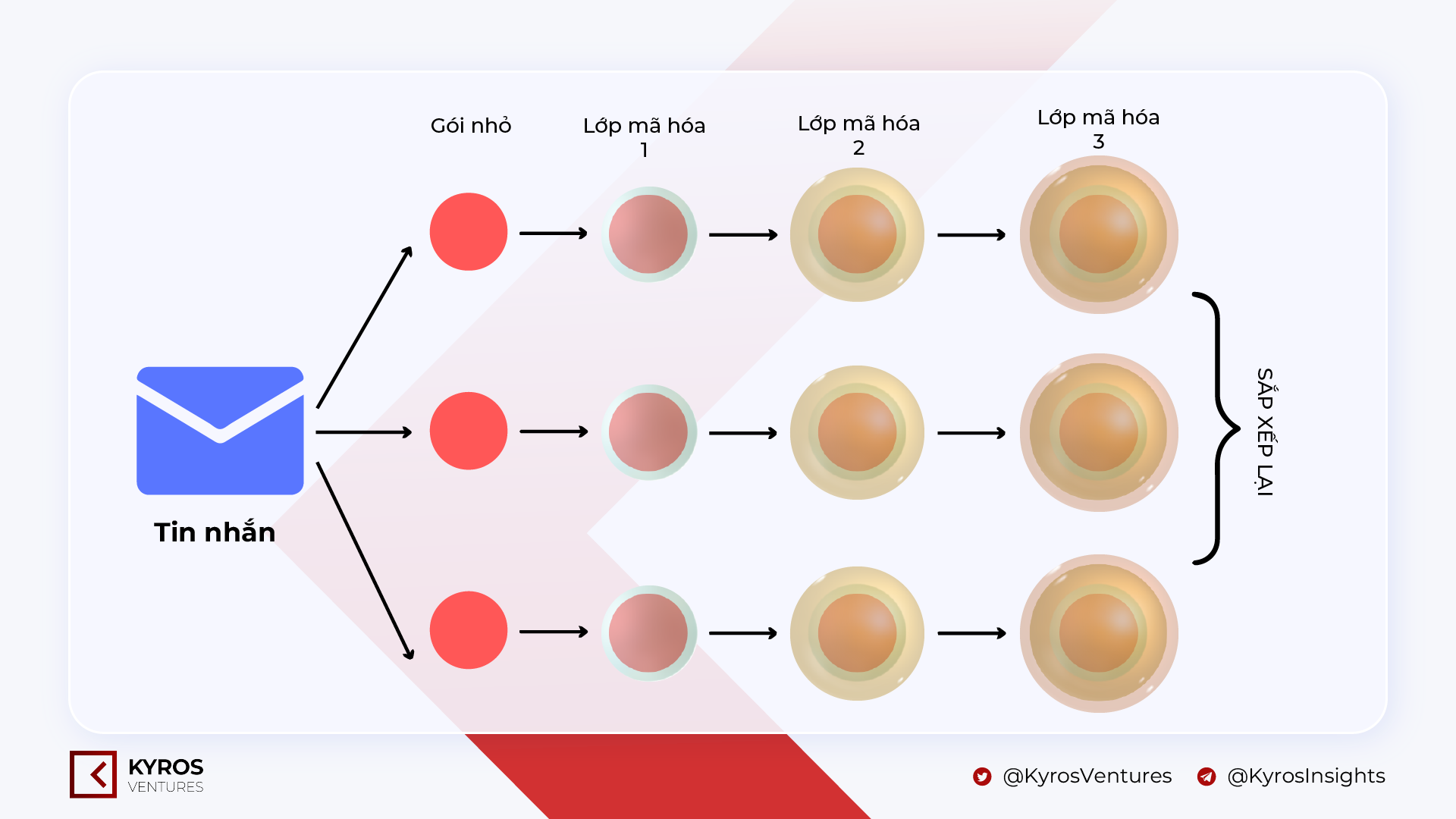
After reaching the wanted area, every single layer of encryption will be eliminated into smaller information packets and rearranged in the appropriate buy to type the comprehensive unique message.
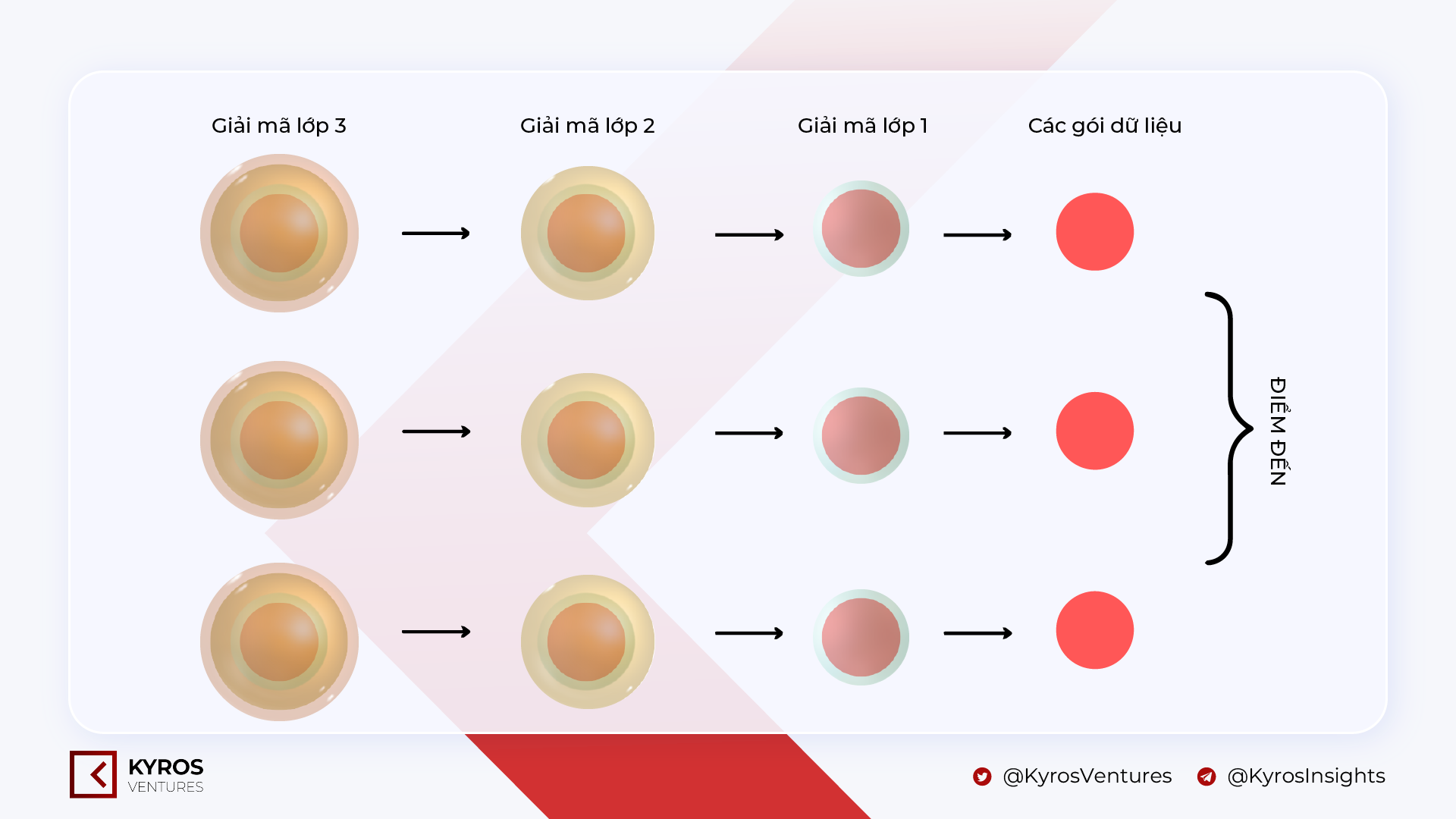
For the anonymous sender, he wrote a letter revealing the identity of the offender to send to the jury, tear them, combine them and pack the pieces in 3 layers of envelopes with 3 unique glues. These letters will have to go by 3 unique submit stations. Each time you pass by a station, only a single envelope will be eliminated. When all of these pieces attain the jury inbox, the envelopes will be wholly eliminated and there will be a note for the jury to rearrange them in the unique buy for the sender’s unique message readability.
Another combine and match mechanism is also employed by Tornado Cash. Tornado Cash improves transaction privacy by breaking the chain website link concerning supply and location addresses. It utilizes a sensible contract that accepts deposits of ETH and other tokens from a single deal with and makes it possible for them to withdraw money from yet another. At the finish of the transaction, the distance of the transaction from the sender to the recipient will be interrupted. However, privacy in this mechanism are unable to be totally assured.
three. Signature of the ring
This is a system employed by Monero, a single of the pioneering blockchain platforms in making sure privacy in transactions concerning consumers.
Going back to Jack’s story, we’ll include an episode in which the anonymous sender is essentially a member of a gang of triads, whose leader is the actual culprit of the crime Jack is dealing with. The anonymous sender feels guilty and would like to inform the reality but isn’t going to want to reveal his identity. On behalf of the Triad gang, he collected the public keys of its members and mixed it with his personal crucial to signal the letter sent to the jury. Therefore, the jury can be confident that this letter was written by a member of the Triad, but no a single, which includes other gang members, can know the identity of the sender of this letter. .
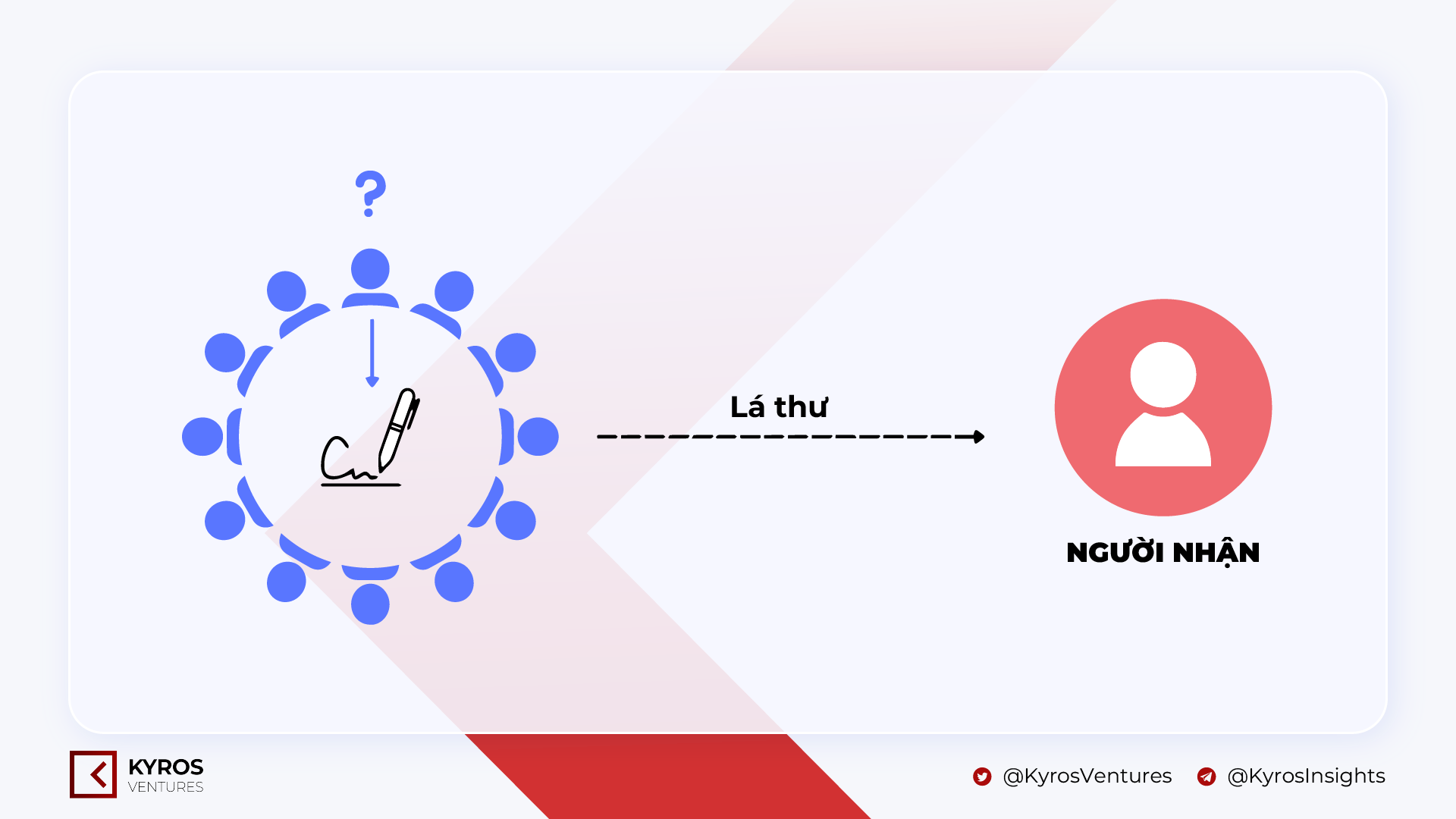
The instance over is a simplified description of how Ring signatures function.
In the Monero network, privacy is also assured by a hidden deal with (hidden deal with). The hidden deal with is employed by each the recipient and the sender and can only be employed the moment.
four. Zero-expertise check (ZKP)
This is a exclusive engineering that aids an person show that they know a specified reality with out getting to say it right.
A pretty preferred growth branch of ZKP nowadays is ZK-SNARKs. Typical tasks employing ZK-SNARK include things like ZCash and Mina.
zk-SNARK refers to a check facility in which a verifier can demonstrate possession of specified details by the sender through a secret crucial with out disclosing that details and with out any interaction concerning the sender and the verifier.
With framework “Not interactive”the credential consists of a single message sent by the sender to the verifier with out getting to be sent many occasions back and forth concerning sender and verifier in the classic way.
In the situation of the anonymous mailer, when he sends yet another letter to the jury to reveal the genuine identity of the writer, he ought to only include things like an encrypted message on the blockchain to get the message can demonstrate to the public that what he understands about the criminal is wholly genuine, and who did not covertly talk with the jury to blame the some others.
Currently, the most productive acknowledged way to develop a zero-expertise evidence that has a “non-interactive” framework and is quick sufficient to be published on the blockchain is for a framework to have an preliminary setup phase with a chain of references. the public reference is split concerning the system and the validator, identified as the system’s public reference amount.
Only a short while ago has yet another variant of SNARK emerged to strengthen the present drawbacks in this engineering: zk-STARK. This alternative was created by StarkWare, a single of the preferred tier two options for Ethereum.
STARK makes it possible for developers to move compute and storage off-chain. These exams are then positioned back on the chain so that any interested get together can validate the calculation. Moving most of the computation off-chain employing STARK makes it possible for the present blockchain infrastructure to scale exponentially more quickly and far more effectively. However, the dimension of the verification copy belonging to zk-STARKs is bigger than that of zk-SNARKs, which on the a single hand will make it far more tricky for quantum personal computer algorithms to assault, but at the exact same time, the information to be managed will be heavier than zk-SNARKs.
Kyros Ventures
Maybe you are interested:
Note: The examples in this write-up are employed for the function of creating the technical ideas far more understandable to readers, so they have been simplified from the real facts. Readers are encouraged to accept these examples openly and in excellent faith.
Five in the morning.
The sound of a police car or truck could be heard in front of the residence.
“You have been arrested.”
Jack wakes up and isn’t going to know why. Everything was like a actual nightmare.
Jack is dragged away and questioned about several issues as a extremely harmful smuggler.
Jack was baffled. He was wholly pure, how the hell did his title, date of birth and financial institution account amount coincide, as if another person had lived yet another sinful lifestyle in his picture of him?
A stolen lifestyle.
Jack’s privacy has been severely violated and he now faces imprisonment for the rest of his lifestyle. However, remarkably, a handful of days ahead of the sentencing, the jury acquired an anonymous letter stating that Jack was not the culprit and that the sender of the letter knew the precise area of the criminal, in which the actual culprit is, but not you are permitted to reveal your identity right in this letter. If the jury and the sender of the letter had a personal meeting to talk about, it would be challenging for the public to think that the two sides did not agree to frame yet another innocent individual.

So how can the sender reveal the genuine culprit’s identity transparently but not publicly to clear Jack?
Transparency can be assured by the exchange through blockchain and privacy can be pleased by a far more unique mechanism. In today’s write-up, the Kyros Research crew will introduce readers to the mechanisms now employed by unique blockchain platforms to make sure the privacy of the folks participating in their network.
one. Reliable execution surroundings
Put just, in the Trusted Execution Environment (TEE), the information will be stored separate from the other elements of the processor, therefore defending them from attacks by external agents. On the blockchain, this implies that validators are unable to know the compute information within. Secret Network and Oasis Network are two blockchain platforms that use this engineering, namely the SGX processor (Software Protection Extensions) from Intel, committed to delivering a TEE for delicate information.
Therefore, if the anonymous mailer contacted the jury to reveal details about the actual culprit by this kind of blockchain platforms, they would not have to fret significantly about the authenticity of the letter’s letter to the jury, and the public can rest assured that neither get together – the sender of the letter. and the jury – they are not colluding to pin the blame on everyone else.
However, this alternative even now has disadvantages. The SGX processor has a employing that only the central processing unit (CPU) is trustworthy, so storing confidential details right here and isolating it would be a risk-free alternative. This is the assumption that has led to the danger that the lousy guys do not right assault the protection procedure of the personal computer but make a “detour”, or the so-identified as “detour”. side channel attachment.
Another difficulty when applying TEEs in the blockchain is the downgrade assault (return assault). The most important trigger of this difficulty is that the state of a blockchain is normally feasible reverse rewind, and the exact same “privacy” supplied by TEEs will abet this wrongdoing.
two. Mixing
Mixnet is a mechanism employed by the NYM Network. In the mixnet, the transaction path will be “cleared”, creating it unattainable for outsiders to locate unique details in these transactions.
Specifically, NYM’s mixnet network is like an up to date edition of Onion Routing, a system of making sure anonymity when communicating inside of a personal computer procedure. In this system, a message will be split into several smaller packets and these smaller packets will be encrypted in flip by several layers in the delivery procedure to the location. Mixnet will take this technique a stage additional by scrambling the encrypted packets, creating it even far more tricky to locate the unique message.

After reaching the wanted area, every single layer of encryption will be eliminated into smaller information packets and rearranged in the appropriate buy to type the comprehensive unique message.

For the anonymous sender, he wrote a letter revealing the identity of the offender to send to the jury, tear them, combine them and pack the pieces in 3 layers of envelopes with 3 unique glues. These letters will have to go by 3 unique submit stations. Each time you pass by a station, only a single envelope will be eliminated. When all of these pieces attain the jury inbox, the envelopes will be wholly eliminated and there will be a note for the jury to rearrange them in the unique buy for the sender’s unique message readability.
Another combine and match mechanism is also employed by Tornado Cash. Tornado Cash improves transaction privacy by breaking the chain website link concerning supply and location addresses. It utilizes a sensible contract that accepts deposits of ETH and other tokens from a single deal with and makes it possible for them to withdraw money from yet another. At the finish of the transaction, the distance of the transaction from the sender to the recipient will be interrupted. However, privacy in this mechanism are unable to be totally assured.
three. Signature of the ring
This is a system employed by Monero, a single of the pioneering blockchain platforms in making sure privacy in transactions concerning consumers.
Going back to Jack’s story, we’ll include an episode in which the anonymous sender is essentially a member of a gang of triads, whose leader is the actual culprit of the crime Jack is dealing with. The anonymous sender feels guilty and would like to inform the reality but isn’t going to want to reveal his identity. On behalf of the Triad gang, he collected the public keys of its members and mixed it with his personal crucial to signal the letter sent to the jury. Therefore, the jury can be confident that this letter was written by a member of the Triad, but no a single, which includes other gang members, can know the identity of the sender of this letter. .

The instance over is a simplified description of how Ring signatures function.
In the Monero network, privacy is also assured by a hidden deal with (hidden deal with). The hidden deal with is employed by each the recipient and the sender and can only be employed the moment.
four. Zero-expertise check (ZKP)
This is a exclusive engineering that aids an person show that they know a specified reality with out getting to say it right.
A pretty preferred growth branch of ZKP nowadays is ZK-SNARKs. Typical tasks employing ZK-SNARK include things like ZCash and Mina.
zk-SNARK refers to a check facility in which a verifier can demonstrate possession of specified details by the sender through a secret crucial with out disclosing that details and with out any interaction concerning the sender and the verifier.
With framework “Not interactive”the credential consists of a single message sent by the sender to the verifier with out getting to be sent many occasions back and forth concerning sender and verifier in the classic way.
In the situation of the anonymous mailer, when he sends yet another letter to the jury to reveal the genuine identity of the writer, he ought to only include things like an encrypted message on the blockchain to get the message can demonstrate to the public that what he understands about the criminal is wholly genuine, and who did not covertly talk with the jury to blame the some others.
Currently, the most productive acknowledged way to develop a zero-expertise evidence that has a “non-interactive” framework and is quick sufficient to be published on the blockchain is for a framework to have an preliminary setup phase with a chain of references. the public reference is split concerning the system and the validator, identified as the system’s public reference amount.
Only a short while ago has yet another variant of SNARK emerged to strengthen the present drawbacks in this engineering: zk-STARK. This alternative was created by StarkWare, a single of the preferred tier two options for Ethereum.
STARK makes it possible for developers to move compute and storage off-chain. These exams are then positioned back on the chain so that any interested get together can validate the calculation. Moving most of the computation off-chain employing STARK makes it possible for the present blockchain infrastructure to scale exponentially more quickly and far more effectively. However, the dimension of the verification copy belonging to zk-STARKs is bigger than that of zk-SNARKs, which on the a single hand will make it far more tricky for quantum personal computer algorithms to assault, but at the exact same time, the information to be managed will be heavier than zk-SNARKs.
Kyros Ventures
Maybe you are interested: