Early this morning (August 2nd), the hottest information in the DeFi local community was absolutely the Nomad assault. While quite a few other bridges have also been visited by hackers, this time the Nomad incident is “a little different” when it comes to some associated names. Then let us consider a search at these names!

Case overview
As reported this morning by Coinlive, Nomad was attacked due to a vulnerability in the authentication of the root message. The particulars and developments of the incident are summarized in the report beneath!
> See extra: Nomad cross-chain bridge breached and “soiled” with extra than $ 176 million in harm
This is not the 1st time the subject of chain bridge contract mistakes has been exploited, but this incident has a large effect, creating me consider of the Poly Network incident extra than a 12 months in the past.
Most of the results of chain attacks are isolated inside the task. However, as quite a few partners use Nomad assets (on distinctive chains), it is inevitable that quite a few names will be hit soon after this incident.
Update:
Peckshield also posted a checklist of wallets concerned in the assault, which include wallets of white hat hackers that they actively hacked to return income to Nomad end users.
#PeckShieldAlert PeckShield discovered ~ 41 scanned addresses ~ $ 152M (~ 80%) in the @nomadxyz_ exploit bridges, which include ~ seven MEV bots (~ $ seven.one million), @RariCapital Harbinger of Arbitrum (~ $ three.four million) and six White Hat (~ $ eight.two million).
~ ten% of these addresses with ENS names having $ six.one million pic.twitter.com/UUjk7ZiiKE– PeckShieldAlert (@PeckShieldAlert) 2 August 2022
“There are about 41 addresses that have withdrawn $ 152 million (~ 80% of the reduction in the Nomad situation). Including seven MEV bots ($ seven.one million), Rari Capital’s hacked wallet (Arbitrum) (~ $ three.four million) and six white hat hackers ($ eight.two million). ten% of these addresses have ENS domains and withdraw $ six.one million. “
Moonbeam
Moonbeam’s Twitter homepage claimed that the assault on the Nomad bridge brought on the destruction of the volume of assets of the Ethereum bridge. The staff also mentioned it is wanting into no matter if there are vulnerabilities in Moonbeam’s supply code.
one / Today there was a protection incident involving the @nomadxyz_ bridges for Moonbeam. Almost all of the assets in Nomad’s Ethereum Mainnet clever contract have been drained. We discovered no proof that the current protection incident was associated to the Moonbeam codebase.
– Moonbeam Network #HarvestMoonbeam (@MoonbeamNetwork) 2 August 2022
Also this morning Moonbeam had to “suspend” the blockchain for four hrs to perform the “Maintenance” procedure. During this time, end users are unable to make income transfers or interact with clever contracts. However, at the time of creating, the servicing procedure has been finished and the Moonbeam staff mentioned that no vulnerabilities associated to the aforementioned assault have been identified.
The servicing mode of the Moonbeam network ended following an investigation that discovered no proof that the current protection incident was associated to the Moonbeam codebase. The chain has been restored to total performance and is now working usually.
– Moonbeam Network #HarvestMoonbeam (@MoonbeamNetwork) 2 August 2022
As a consequence, Nomad is a important bridge platform on the Moonbeam ecosystem, and the theft of most of the Ethereum bridgehead protection assets can impact the worth of some bridgehead assets.
Colleague
Connext is a staff that has a shut connection with Nomad. Many sources feel that Connext derives its liquidity from Nomad and could endure huge losses soon after this incident. However, Arjun (task representative) mentioned that Connext only merchants madUSDC assets (i.e. USDC certificates on the Nomad bridge).
We are conscious of the exploit of the @nomadxyz_ contracts on Ethereum.
Connectext end users are not right impacted by this exploit.
However, madAsset held by end users on Moonbeam, Milkomeda and Evmos could now not be backed by matching assets on Ethereum.
1st/
– Next | ✖componibility of the chain (@ConnextNetwork) 2 August 2022
“We have been informed of an assault on the Ethereum contract. Connext end users are not right impacted by this incident, but madAsset (asset certificates) held by end users on Moonbeam, Milkomeda and Evmos could not be absolutely supported by assets on Ethereum.
Connext also mentioned the staff contacted bridge partners to suspend the rotation of madAsset’s assets to stay clear of losses.
Evmos
Evmos is the rarest situation, when the rate of the EVMOS coin skyrocketed soon after the Nomad assault.
$ EVMOS is pumping tricky soon after the Nomad bridge exploit
Everyone tries to convert their Nomad $ USDC fantastic $ EVMOS pic.twitter.com/8LZbgIqoIc
– Yield God (@YieldGod) 1 August 2022
The explanation for this fluctuation is that madUSDC has misplaced its rate anchor at the Ethereum beachhead, major quite a few men and women to check out to promote this asset to EVMOS to stay clear of the asset’s reduction in worth. However, the lack of liquidity and a huge variety of end users landed, creating the rate of EVMOS to rise quickly.
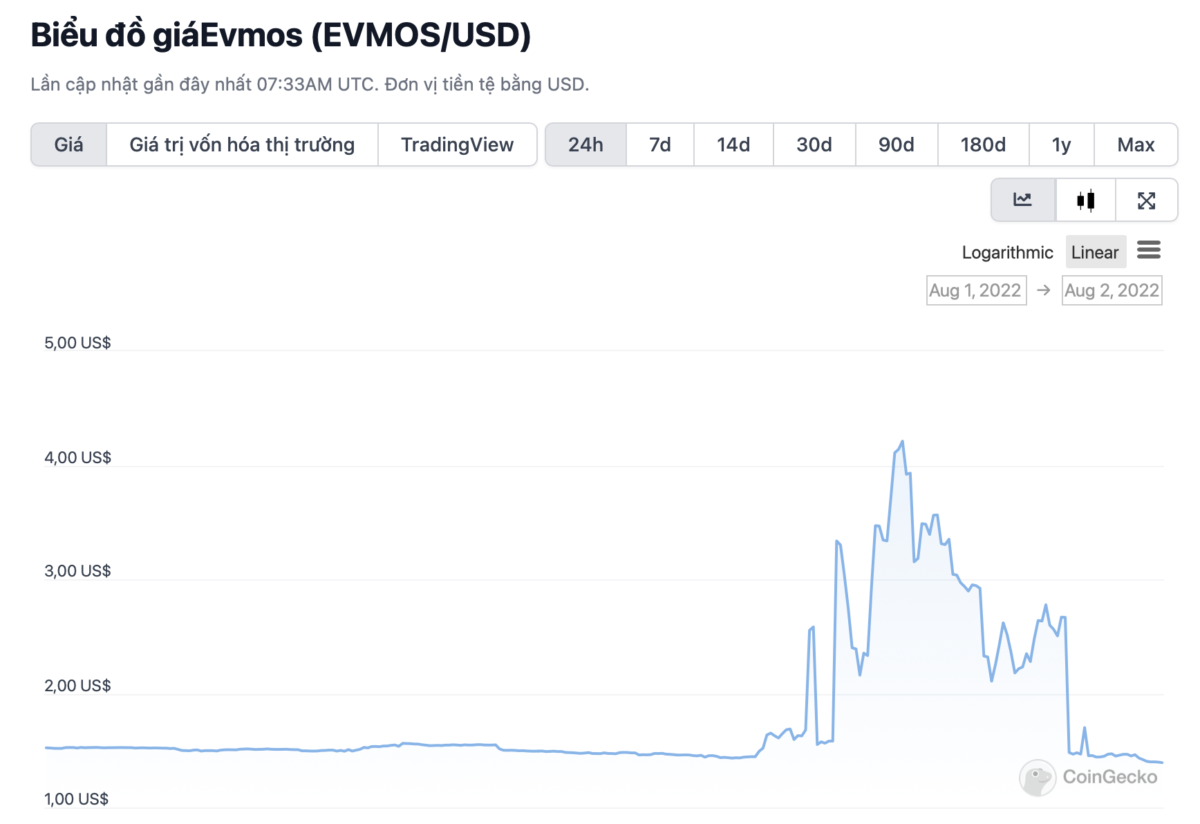
However, this move immediately cooled down afterwards as end users attempted to move assets to other chains.
A couple of hrs in the past the Nomad ERC20 bridge contract was exploited. Most of the assets have been dried up. We are doing work closely with the Nomad staff and will get hold of you as quickly as we have extra information and facts.
Rest assured, the Evmos chain functions effectively. This is strictly a bridge exploit. (one/three)
– Evmos is employing ☄️ (@EvmosOrg) 2 August 2022
The Evmos staff mentioned that this vulnerability is not associated to the network and that the Evmos chain is nevertheless working usually.
finish
So, as of the time of creating, there have been no extra Nomad-influenced names announced. As stated over, this situation does not come up due to the nature of the “cross chain” but is a challenge resulting from the contract protection error, which can happen with any series of DeFi goods. .
However, yet again and yet again, the danger of these goods is that when attacked, they can immediately spread to neighboring chains as properly as associated goods.
The newest updates on this incident will be immediately sent to readers by Coinlive!
Synthetic currency 68
Maybe you are interested: