Bug Bounty is an outdated but new idea, in particular when launched to the Web3 playground. Continuity of protection attacks in 2022 highlighted the relevance of bug hunting packages. In this write-up, Coinlive will stroll you by the Bug Bounty idea, exceptional challenges, and new issues whilst migrating to Web3 with readers.

What is Bug Bounty?
Bug Bounty is a protection plan organized by tasks, providers or third events to appeal to the neighborhood to “detect” and report protection holes (bugs) in technological methods. In specific, a bonus will be offered to individuals who obtain bugs, in standard the far more severe the error, the greater the reward.
A typical Web3 debugger consists of two principal objects as follows:
- Organizational unit: The task itself or a third get together organizes it. This is the unit accountable for creating and announcing the plan and awarding the awards.
- White hat hackers: As folks who participate in bug hunting, they can come from quite a few distinctive backgrounds from cyber protection authorities, technical prospects (SREs), protection consultants, and so forth.
Bug Bounty is a bridge connecting two objects, a task (needing protection administration) and a white hat hacker (in search of earnings with very good motive). Some reliable Web3 Bug Bounty organizing platforms include things like: Immune (established in 2020) e HackenProof (established in 2017).
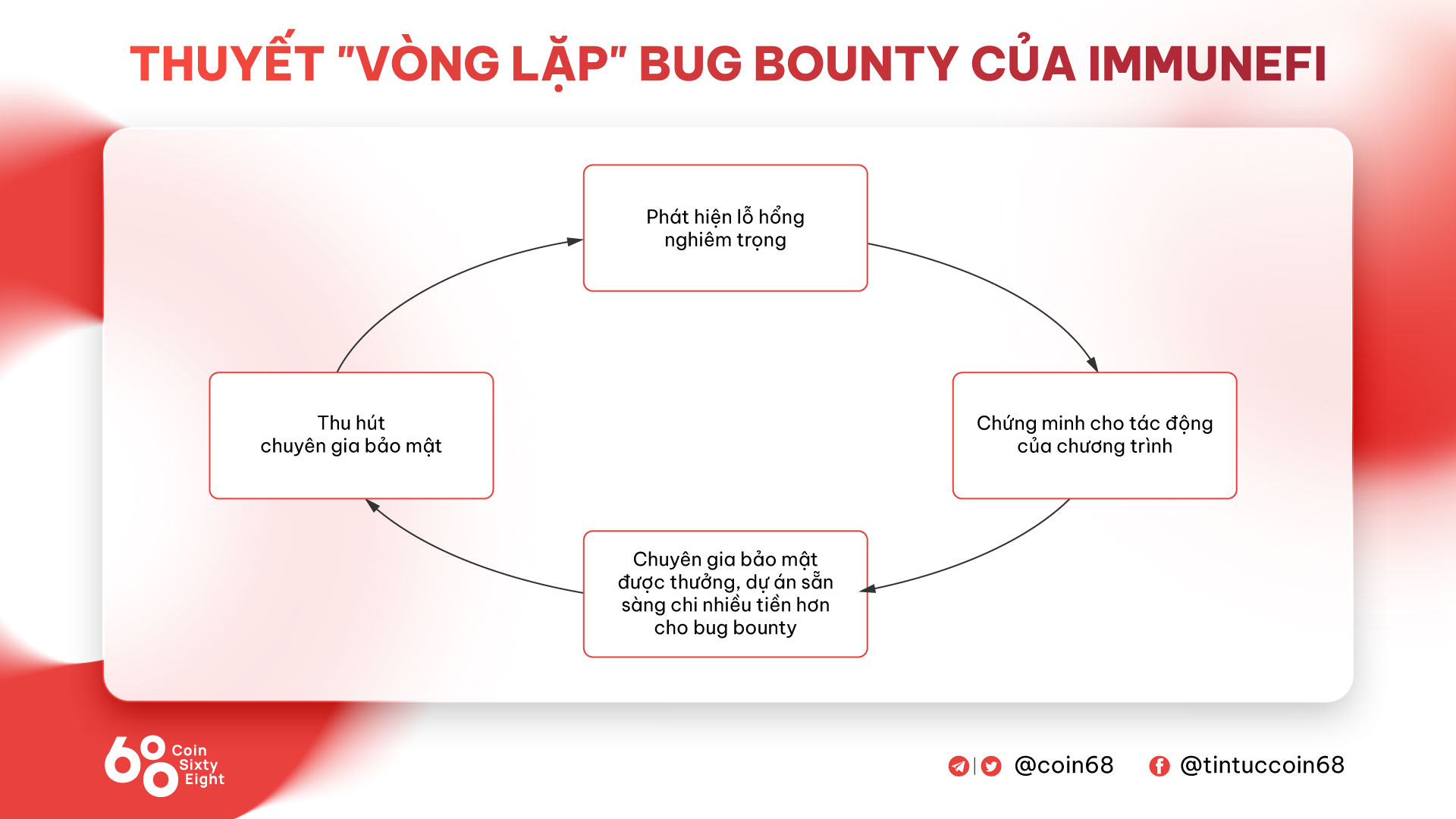
According to Immunefi, their working model will include things like a self-healing cycle as follows:
- The task attracts protection authorities
- Security authorities support detect large-danger vulnerabilities
- This demonstrates the affect of significant rewards
- Security authorities are very well rewarded, other tasks are ready to commit large on bug bounty rewards and go back to phase one.
Days of “groping in the dark”
This time many years in the past, Bug Bounty Web3 was dealing with challenges like:
- The construction of the bug hunting plan is not nonetheless defined but is regularly currently being fine-tuned and is hard to sustain
- There are incredibly number of organized packages, with constrained prizes
- Hackers only pick out to participate in the large bounty plan
- Always in a state of “thirst for talent”.
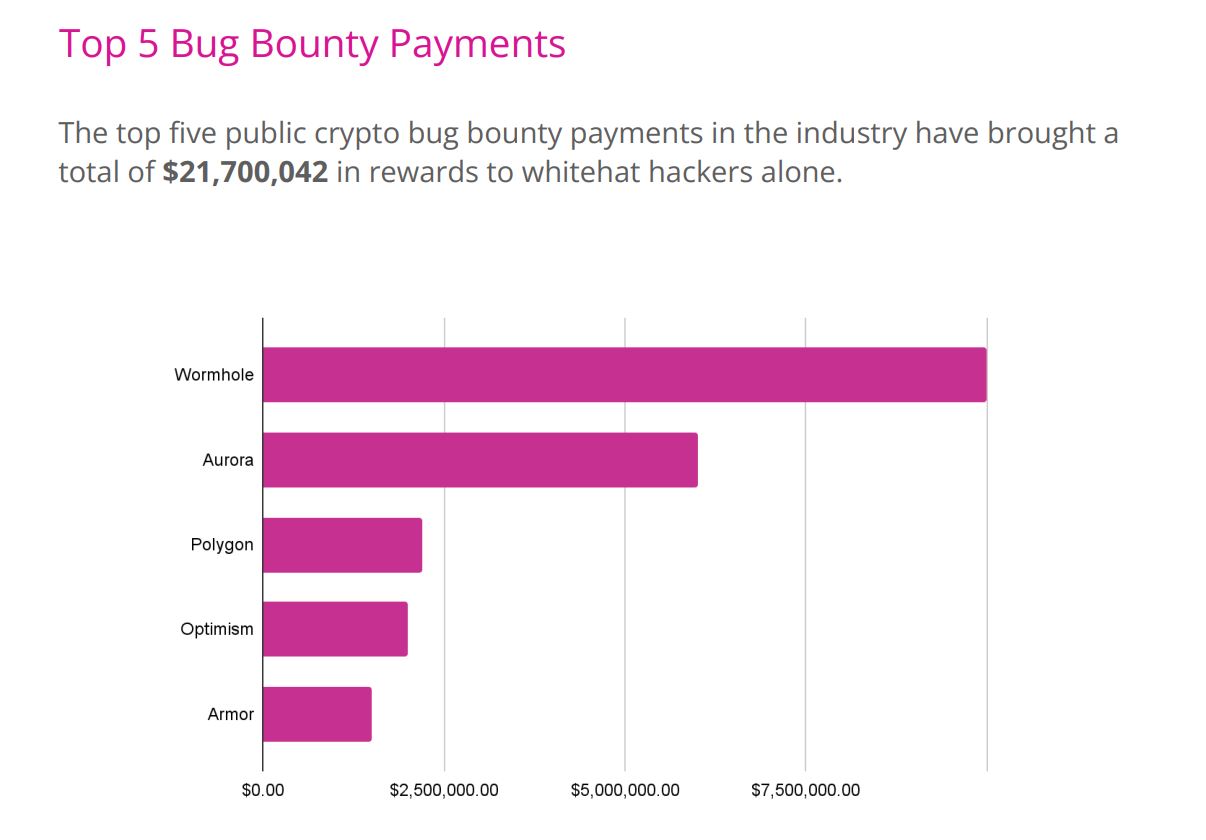
Importantly, the Bug Bounty in Web3 is in large demand. To give a concrete illustration, whilst Google (representing Web2) complete $eight.seven million for bug-hunting packages in 2021, in one particular plan run, the platform Wormhole cross-chain paid a white hat hacker $ten million for procedure-broad error detection.
The motive for the dimension disparity of Web2 and Web3 is that vulnerabilities in the Web3 area can very easily lead to direct reduction of money, primarily due to the sum of coins stored in wise contracts.
Bug Bounty in the current
Experiencing quite a few ups and downs with the cryptocurrency marketplace in 2021-2022, the worth of “bug hunting” packages is progressively currently being recognised. Being regarded by the tasks to invest and “spend more”, the investment money agreed to pour capital into the OU.
In 2022, the biggest bug bounty platform in the cryptocurrency business is Immunefi awarded a complete of $52 millionlogged the biggest bounty in Web3 Bug Bounty historical past.
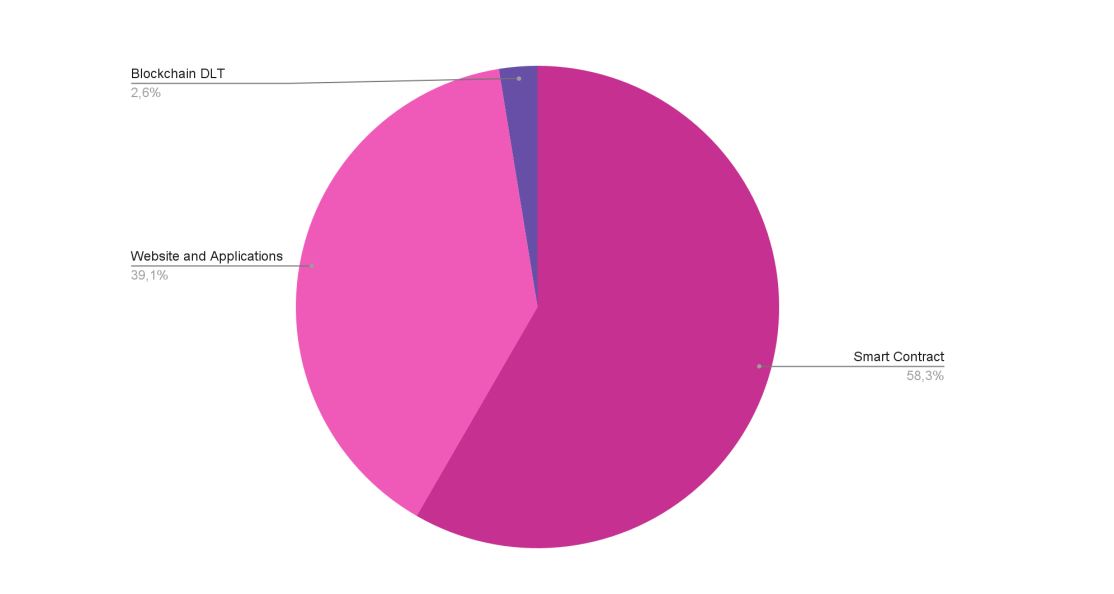
The unit also reported that the bulk of identified vulnerabilities are in the wise contract layer, followed by the site and application layer, whilst blockchain protocols are seldom flawed. One noteworthy level is that the severity of mistakes is also split evenly, with no degree representing the bulk, which signifies that there is no concealment in the mistakes reported by white hat hackers.
In addition, hundreds of packages with up to eight-digit bonuses have been held on DeFi. Approximately $150 million is accessible solely for awarding. According to Immunefi’s estimates of the expense of danger a identified vulnerability could induce, Bug Bounty packages have saved far more than $forty billion for DeFi tasks and the cryptocurrency business, most notably in connected crashes involving Polygon and Solana.
The issue when Bug Bounty entered Web3
- Insect: Bugs in Web3 are not the very same as bugs in Web2 and there are quite a few variations. For illustration, in Web2, hackers will recognize vulnerabilities in computer software (CWE), whilst Web3 will recognize vulnerabilities in wise contracts (SWC)
- Attack assortment: The assault surface on a technological procedure is incredibly significant and hard to measure, whilst the programming code of the blockchain is more and more complicated
- Thirst for talent: Currently, the human assets operating in Web3 are nevertheless not as abundant as in the regular computing discipline. Combined with the complexity of the blockchain and the time and hard work needed, the final results seem to be incredibly puzzling for programmers hunting to obtain a bug bounty reward simply because the bug is unlikely to have been detected or fixed. attempt in this natural environment.
- Mathematical talent: A Web3 protocol specialist participant may perhaps not be very good at bridge remedies and vice versa. However, each are needed for a researcher to detect vulnerabilities in how the protocol and the bridge perform collectively. This demonstrates that it will be needed to strategy instruction, comprehensively and systematically, to produce a sturdy human resource.
Potential bug bounty in Web3
Based on Immunefi CEO Mitchell Amador’s vision, Bug Bounty packages will have a bounty worth of somewhere around $one billion by 2025. Hundreds of hundreds of thousands of bucks in bounties will be paid each and every 12 months, therefore propelling a range of protection routines dungeons in area. The CEO expects each and every main task to run its personal qualified rewards plan, with the purpose of developing incentives to appeal to white-hat hackers to participate in testing and support the task avoid potential protection assault hazards.
Ari
Bug Bounty is an outdated but new idea, in particular when launched to the Web3 playground. Continuity of protection attacks in 2022 highlighted the relevance of bug hunting packages. In this write-up, Coinlive will stroll you by the Bug Bounty idea, exceptional challenges, and new issues whilst migrating to Web3 with readers.

What is Bug Bounty?
Bug Bounty is a protection plan organized by tasks, providers or third events to appeal to the neighborhood to “detect” and report protection holes (bugs) in technological methods. In specific, a bonus will be offered to individuals who obtain bugs, in standard the far more severe the error, the greater the reward.
A typical Web3 debugger consists of two principal objects as follows:
- Organizational unit: The task itself or a third get together organizes it. This is the unit accountable for creating and announcing the plan and awarding the awards.
- White hat hackers: As folks who participate in bug hunting, they can come from quite a few distinctive backgrounds from cyber protection authorities, technical prospects (SREs), protection consultants, and so forth.
Bug Bounty is a bridge connecting two objects, a task (needing protection administration) and a white hat hacker (in search of earnings with very good motive). Some reliable Web3 Bug Bounty organizing platforms include things like: Immune (established in 2020) e HackenProof (established in 2017).
According to Immunefi, their working model will include things like a self-healing cycle as follows:
- The task attracts protection authorities
- Security authorities support detect large-danger vulnerabilities
- This demonstrates the affect of significant rewards
- Security authorities are very well rewarded, other tasks are ready to commit large on bug bounty rewards and go back to phase one.

Days of “groping in the dark”
This time many years in the past, Bug Bounty Web3 was dealing with challenges like:
- The construction of the bug hunting plan is not nonetheless defined but is regularly currently being fine-tuned and is hard to sustain
- There are incredibly number of organized packages, with constrained prizes
- Hackers only pick out to participate in the large bounty plan
- Always in a state of “thirst for talent”.
Importantly, the Bug Bounty in Web3 is in large demand. To give a concrete illustration, whilst Google (representing Web2) complete $eight.seven million for bug-hunting packages in 2021, in one particular plan run, the platform Wormhole cross-chain paid a white hat hacker $ten million for procedure-broad error detection.
The motive for the dimension disparity of Web2 and Web3 is that vulnerabilities in the Web3 area can very easily lead to direct reduction of money, primarily due to the sum of coins stored in wise contracts.
Bug Bounty in the current
Experiencing quite a few ups and downs with the cryptocurrency marketplace in 2021-2022, the worth of “bug hunting” packages is progressively currently being recognised. Being regarded by the tasks to invest and “spend more”, the investment money agreed to pour capital into the OU.
In 2022, the biggest bug bounty platform in the cryptocurrency business is Immunefi awarded a complete of $52 millionlogged the biggest bounty in Web3 Bug Bounty historical past.

The unit also reported that the bulk of identified vulnerabilities are in the wise contract layer, followed by the site and application layer, whilst blockchain protocols are seldom flawed. One noteworthy level is that the severity of mistakes is also split evenly, with no degree representing the bulk, which signifies that there is no concealment in the mistakes reported by white hat hackers.

In addition, hundreds of packages with up to eight-digit bonuses have been held on DeFi. Approximately $150 million is accessible solely for awarding. According to Immunefi’s estimates of the expense of danger a identified vulnerability could induce, Bug Bounty packages have saved far more than $forty billion for DeFi tasks and the cryptocurrency business, most notably in connected crashes involving Polygon and Solana.
The issue when Bug Bounty entered Web3
- Insect: Bugs in Web3 are not the very same as bugs in Web2 and there are quite a few variations. For illustration, in Web2, hackers will recognize vulnerabilities in computer software (CWE), whilst Web3 will recognize vulnerabilities in wise contracts (SWC)
- Attack assortment: The assault surface on a technological procedure is incredibly significant and hard to measure, whilst the programming code of the blockchain is more and more complicated
- Thirst for talent: Currently, the human assets operating in Web3 are nevertheless not as abundant as in the regular computing discipline. Combined with the complexity of the blockchain and the time and hard work needed, the final results seem to be incredibly puzzling for programmers hunting to obtain a bug bounty reward simply because the bug is unlikely to have been detected or fixed. attempt in this natural environment.
- Mathematical talent: A Web3 protocol specialist participant may perhaps not be very good at bridge remedies and vice versa. However, each are needed for a researcher to detect vulnerabilities in how the protocol and the bridge perform collectively. This demonstrates that it will be needed to strategy instruction, comprehensively and systematically, to produce a sturdy human resource.
Potential bug bounty in Web3
Based on Immunefi CEO Mitchell Amador’s vision, Bug Bounty packages will have a bounty worth of somewhere around $one billion by 2025. Hundreds of hundreds of thousands of bucks in bounties will be paid each and every 12 months, therefore propelling a range of protection routines dungeons in area. The CEO expects each and every main task to run its personal qualified rewards plan, with the purpose of developing incentives to appeal to white-hat hackers to participate in testing and support the task avoid potential protection assault hazards.
Ari